In the digital age, the push for security has long been outpaced by the drive for efficiency. Companies focused on developing code are often expected to make releases incredibly frequently – potentially even several times a day – just to remain competitive. Approaches such as DevOps and Agile have helped spearhead this speed, cutting down on obstructive siloed thinking and encouraging teams and departments to collaborate for the sake of achieving crucial business goals.
However, this has not been without its drawbacks. Efficient methodologies, combined with scaling technologies such as cloud environments and serverless architectures, have outgrown traditional security practices. This can leave organizations and their clients extremely vulnerable, with poorly-managed security leaving back doors that keep secrets and data within easy reach of criminals.
This is primarily because, for a long time, security simply did not get as much attention in IT as it does now. It was treated as a last-minute consideration – a problem that could be solved with reactive tactics. Experts such as white-hat hackers would highlight issues for companies, only for them to take on a see-no-evil approach. After all, it was cheaper and easier to hope that worst-case scenarios would remain speculative.
Not that such an approach holds water anymore. These days, stories of hacker attacks and data breaches, along with the advent of the policies like GDPR, have turned security into an issue of utmost importance. All departments are now expected to make security considerations to at least some extent. But with more coding required now than ever before, many organizations are finding themselves having to choose between the efficiency that sustains them and the security that protects their customers.
The truth of the matter is that it is often much cheaper and easier to fix security issues sooner, rather than later. Not only can this help to ensure that vulnerable code is not released, but it can also give different teams more time to locate potential flaws. By fixing problems early on, less has to be changed, helping companies to avoid expensive delays or bottlenecks. Finally, building security into code can both improve its quality and help to provide PR boosts to careful organizations.
So, how can an organization maximize security in modern IT without having to sacrifice speed?

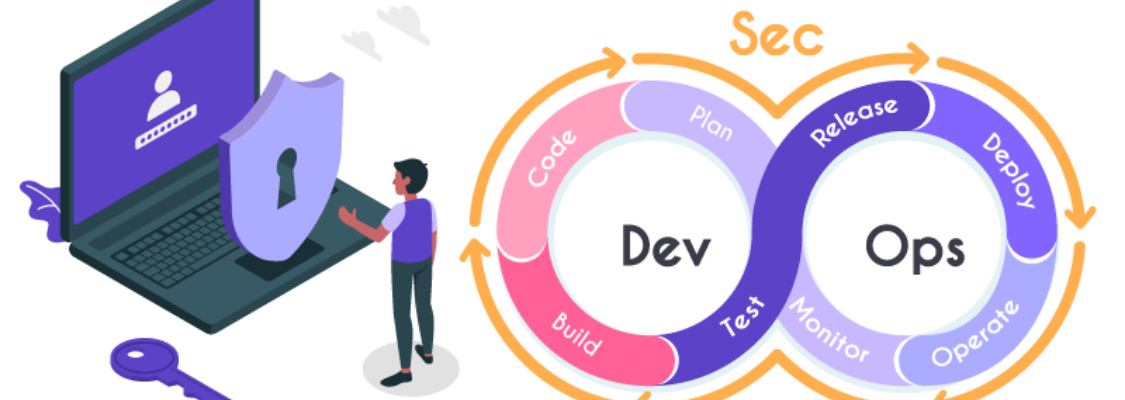
Security and DevOps
As impressive as the traditional DevOps approach is, introducing security into DevOps process chains can cause significant delays. To put it simply, DevOps is too fast for traditional security. Manual vulnerability assessments cause lag, and ultimately reduce deployment rates.
‘SecOps’ was created in response to this. It follows similar principles to DevOps, combining two functions in order to improve efficiency, awareness, and reliability. It places a special emphasis on compliance, as well as having security experts and automated security tools contribute to every stage of the development cycle.
SecOps enhances collaboration by providing teams with tools and training that offers insight into preventing security threats and repairing vulnerabilities within systems as soon as they are discovered. SecOps tools also supply users with constant streams of relevant data, helping to boost their operational intelligence of the systems they monitor.
Combining DevOps and SecOps
‘DevSecOps’ is a combination of DevOps and SecOps, and makes security a priority for both development and operational teams. It aims to maintain the efficiency offered by DevOps principles whilst also enabling security and compliance. Similarly to how DevOps has teams collaborate throughout the lifecycle of a project, DevSecOps embeds security into the product development lifecycle and beyond, including the stages of inception, design, build, test, release, support, and maintenance. It creates transparent policies that everyone can follow in order to take shared ownership of security.
A key advantage of DevSecOps is that it takes a great deal of the workload away from security professionals. This can give them time to develop a more extensive understanding of other key processes, complementing the culture of collaboration that has always been inherent to the DevOps methodology. It also encourages developers to utilize more secure coding practices while simultaneously having operations staff put greater emphasis on compliance.
By successfully integrating security considerations into DevOps’ collaborative culture, organizations can enjoy more secure software, reduced recall rates, improved reputations, and decreases in costs that come from repairs and delays.

The elements of SecOps and DevSecOps
Several tools and processes can be used for successfully integrating security into the DevOps methodology:
- Compliance monitoring – This is implemented during the early stages of the development lifecycle. Various teams and departments are taught about basic compliance issues, while security practitioners monitor the situation throughout. This level of dedication is crucial for avoiding the harsher penalties of the GDPR
- Threat investigation – When using DevSecOps, threats are dealt with as soon as they are highlighted. Removing them early on in the development cycle can significantly cut down on any resulting costs and setbacks
- Vulnerability assessment – DevSecOps teams scan for, assess, and remediate all vulnerabilities BEFORE deployment using methods such as penetration testing. They also continue after the point of deployment in order to find issues which need to be patched or repaired
- Automated code analysis – Automation is crucial for scaling security processes to cover all development and operations work. It can help to identify threats, infrastructural issues, problematic code, and dangerous vulnerabilities. Most importantly, it can help to ensure that security measures match the speed of DevOps practices
- Segmenting networks – This involves grouping resource and application servers into separate units for the sake of reducing the number of potential access points for attacks
- Privileged access management – By removing administrator privileges from end-user machines and storing privileged account details as securely as possible, organizations can limit the number of opportunities for internal or external attackers to take advantage of bad code
- Secrets management – Embedded credentials are removed from code, scripts, files, tools, service accounts, cloud platforms, and so on. Passwords are then stored in a centralized location
All our DevOps online courses are fully accredited by the DevOps Institute. You can view all our accredited DevOps courses here, or contact Good e-Learning today to speak to a member of our team!